Security has been elevated to a top priority in the field of software development. Organizations are becoming more and more aware of the necessity for a proactive and all-encompassing strategy for software security as a result of the increase in cyber threats and data breaches. DevSecOps, a new paradigm where security is incorporated into every step of the software development lifecycle, is the result of this insight. We will look at how DevSecOps transforms security architecture in this post, boosting the protection of digital assets and assuring the delivery of safe and reliable software solutions.
Table Of Contents 👉
DevSecOps: What Is It?
The whole stack is DevSecOps: Including network, host, container, server, cloud, mobile, and application security, DevSecOps covers the full IT stack. Since each of these levels is progressively being replaced by software, DevSecOps services must place a high priority on application security. The complete software development lifecycle, including development and operations, is covered by DevSecOps. While monitoring and responding against assaults are the primary goals of operations, discovering and avoiding vulnerabilities are the emphasis of security throughout development. Successful DevSecOps projects depend on an understanding of the various security tasks and their value to the enterprise.
Organizations can gain from working with a Kubernetes consulting company to implement DevSecOps successfully. A key factor in facilitating the seamless integration of security practices into the development pipeline is the container orchestration platform Kubernetes. A skilled Kubernetes consulting firm can offer insightful advice, best practices, and direction on how to integrate security into every step of the DevSecOps process. Organizations can strengthen their overall security posture, implement DevSecOps successfully, and reduce risks throughout the software development lifecycle by utilizing the skills of a Kubernetes consulting firm.
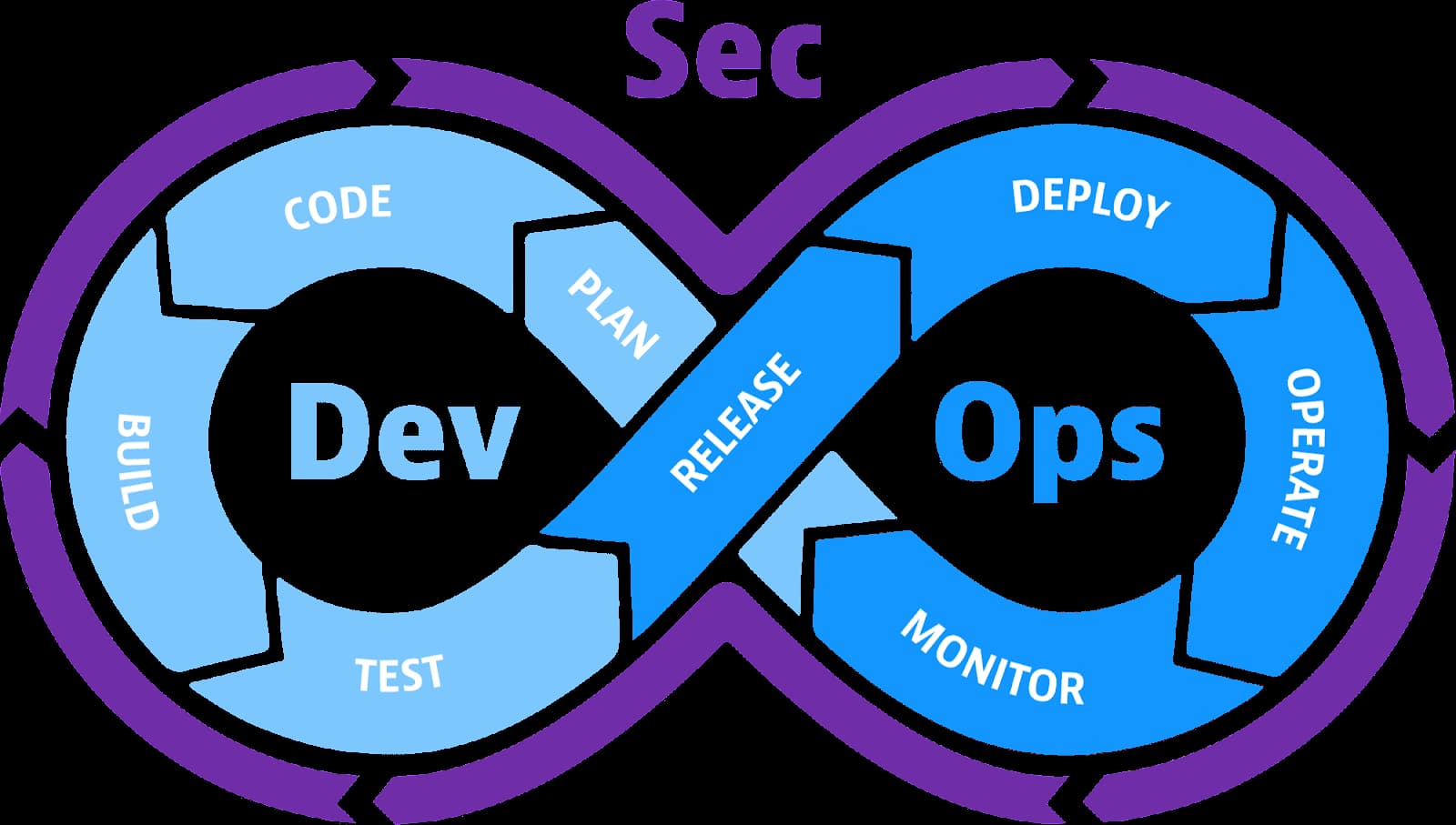
DevOps vs DevSecOps
The goal of DevOps methods is to automate and collaborate to accelerate and simplify the development process. DevOps offers considerable advantages over conventional development approaches by fostering closer collaboration between the development and operations teams, cutting down on development cycles, and automating when appropriate.
In contrast to DevOps, DevSecOps involves the security team in this cooperation early on in the SDLC. In the past, security was mostly dealt with during the SDLC Testing phase, when development was almost all finished, and the cost of addressing issues was significant. The cost of patching vulnerabilities is decreased when security is built in from the beginning, and the likelihood that security will be incorporated rather than “bolted on” is increased.
Important Components of a DevSecOps Environment
Shifting Left: Security from the Start
The notion of “shifting left,” or incorporating security practices early in the software development lifecycle, is central to DevSecOps. Developers may address possible vulnerabilities before they get established in the code by adding security requirements and testing from the beginning of the design process. This proactive strategy saves the expense and time involved with addressing security vulnerabilities later in the development cycle.
An Iterative Approach to Continuous Security Testing
Continuous security testing is another critical part of DevSecOps. Traditional security testing was often conducted in isolated cases, causing delays and impeding adaptability. DevSecOps, on the other hand, encourages the use of automated security testing solutions that can be smoothly incorporated into the development process. These tools scan the code for vulnerabilities, assess dependencies, and offer developers real-time feedback. As a consequence, security becomes an iterative process, enabling teams to fix concerns quickly and enhance the software’s overall security posture.
Breaking Down Silos in Collaboration and Communication
DevSecOps encourages cooperation and communication across teams in development, operations, and security. Organizations may use the aggregate knowledge and skills of each team by breaking down silos and facilitating cross-functional cooperation. Security specialists collaborate closely with developers, advising them on safe coding methods and assisting them in understanding the most recent threats and mitigation approaches. Similarly, developers participate in security testing and provide insights into their code, ensuring that security problems are handled throughout the development process.
Infrastructure as Code: Environmental Security
DevSecOps has an impact on the infrastructure as well as the application layer. Security architecture now spans the whole technological stack, thanks to the advent of cloud computing and infrastructure as code (IaC) approaches. Using technologies like Terraform or CloudFormation, security teams interact with operations and development teams to build and deploy safe infrastructure settings. This method enables security rules and settings to be version-controlled, auditable, and incorporated into the development process, assuring the application’s security.
Conclusion
Traditional security methods simply do not work effectively in the fast-paced world of today. A safe product demands an integrated and comprehensive solution, and DevSecOps is the ideal option, given the nature of recent current security attacks.
Related Stories:
