Cybersecurity expert Jeremiah Fowler found a poorly configured cloud server that contained a staggering 184 million login credentials, likely gathered through infostealer malware.
Fowler uncovered an unprotected database with more than 184 million unique usernames and passwords. His findings, shared with reporters, revealed that this massive data leak totaled about 47.42 gigabytes.

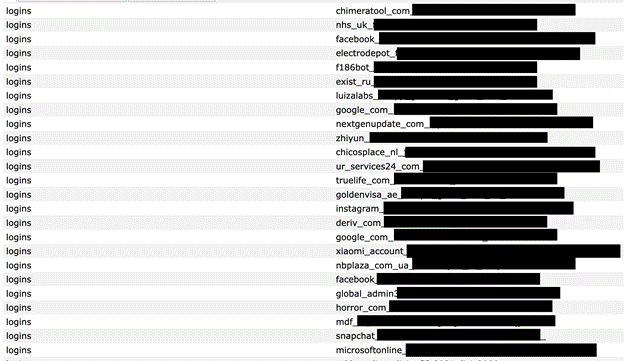
This unprotected database lacked any password or encryption, storing login details for a variety of online services.
These included well-known email providers, major tech companies like Microsoft, and social media platforms such as Facebook, Instagram, Apple, Google, Snapchat, and Roblox.
The leak was particularly concerning as it also included sensitive information for bank accounts, health services, and even government websites from multiple countries, putting many people at significant risk.
Fowler validated some of the records by reaching out to individuals whose emails appeared in the database, and many confirmed that their passwords were indeed listed.
After making this discovery, Fowler promptly alerted the hosting provider, resulting in the database being taken offline. The IP address of the database linked to two domain names, one of which seemed to be unregistered. Due to private registration details, the actual owner of this data remains unknown.
It is still uncertain how long this sensitive information was exposed or whether other malicious actors had accessed it before it was discovered.
The hosting provider withheld customer information, making the purpose of the data collection unclear, whether it was intended for criminal activities or legitimate research.
From the evidence, it appears that the database was owned by cybercriminals who were gathering data using infostealers, ultimately leading to their own database being exposed.
Infostealers are commonly used tools among criminals, and reports indicate that even organizations like the US military and FBI have suffered breaches due to these malware programs, which can be purchased for as little as $10.
Infostealer malware is designed to secretly gather sensitive information from infected computers, primarily targeting login credentials saved in web browsers, email applications, and messaging services.
Recent incidents highlight a coordinated effort by Microsoft and Europol to dismantle the infrastructure of Lumma Stealer, a malware that has infected over 394,000 Windows computers globally. This situation underscores the type of threat revealed by Fowler’s findings.
Fowler analyzed the exposed data, noting that it consisted mainly of raw credentials and URLs for login pages, which aligns perfectly with the information infostealers like Lumma are intended to capture.
Although he could not pinpoint the exact malware responsible for the leak, the nature of the data strongly suggests that infostealer methods were used.
It is not uncommon for cybercriminals to inadvertently expose their own servers. Just a few months ago, reports indicated that the notorious ShinyHunters and Nemesis hacking groups targeted and extracted data from exposed AWS buckets, only to accidentally leak their own data in the process.
The presence of millions of login details poses a significant threat for cybercriminals, who can exploit this information through techniques like credential stuffing attacks and account takeovers. Such attacks enable criminals to access personal information, leading to identity theft or financial fraud.
The leaked data might also include business credentials, raising the risk of corporate espionage and even compromising sensitive government networks.
Knowing an email and an old password can make phishing and social engineering attacks more believable.
Fowler recommends users refrain from using email accounts to store sensitive information, frequently update passwords, particularly following security breaches, avoid reusing passwords across multiple accounts, enable Two Factor Authentication (2FA), and turn on notifications to monitor suspicious login attempts.
Other Stories You May Like
