CISA, NSA and FBI today revealed the top security flaws exploited by hackers backed by China’s People’s Republic of China (PRC). These hackers are targeting government and critical infrastructure networks. In a joint advisory, the three federal agencies stated that Chinese-sponsored hackers target U.S. networks and tech companies to steal intellectual property and gain access to sensitive networks.
The advisory states that the NSA, CISA and FBI continue to evaluate the state-sponsored cyber activities of the PRC as one of the most significant and dynamic threats to U.S. government networks and civilian networks.
“This joint CSA draws on the FBI, NSA, CISA and FBI reports to inform federal, state, local, tribes and territorial (SLTT), government officials; critical infrastructure including the Defense Industrial Base Sector; as well as private sector organizations, about noteworthy trends and persistent techniques, techniques and procedures (TTPs).
This advisory contains recommended mitigations for all security flaws commonly exploited by threat actors in China. It also includes detection methods and vulnerable technology to assist defenders in detecting and blocking incoming attacks.
According to the FBI, CISA and NSA, the following security flaws have been most commonly exploited since 2020 by Chinese-backed state hackers.
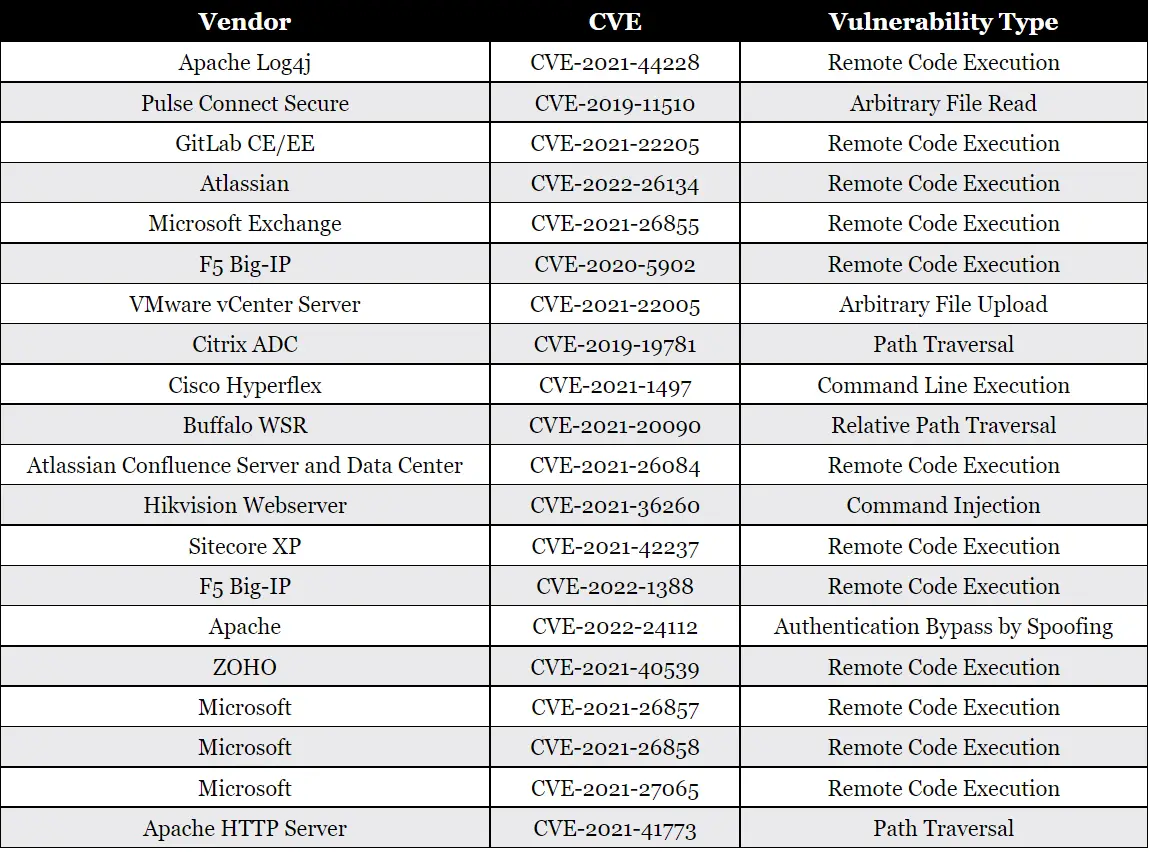
CISA, FBI, NSA and NSA urged U.S. governments and allied countries to use the following mitigation strategies to protect against Chinese-sponsored cyberattacks.
These federal agencies recommend that organizations apply security patches as soon and as often as possible. They also advise using phishing-resistant multifactor authentication (MFA) whenever possible to replace any end-of-life network infrastructure not receiving security patches.
They recommend that you move towards Zero Trust security and enable robust logging on internet-exposed services to detect attacks as quickly as possible.
This joint advisory today follows two others that share information about tactics, techniques and procedures (TTPs) used by Chinese-backed threats groups (in 2021) and public vulnerabilities they exploit in attacks (in 2020).
They also revealed in June that Chinese state hackers had compromised major telecom companies and network service providers to steal credentials and harvest data.
The U.S. Government issued a Tuesday alert regarding state-backed hackers stealing data from U.S. defense contractors using a custom CovalentStealer malware and the Impacket framework.
Today’s Trending Stories:
